The Rise of Technology and Its Effect on Search and Seizure Analysis: The Constitutionality of Geofencing Warrants Under the Supreme Court’s Fourth Amendment Jurisprudence
By

By
Tyler J. Schembri[1]*
In November of 2022, four roommates in Moscow, Idaho were brutally murdered in the middle of the night, sending shockwaves through the town. The killer left the remaining two roommates unscathed before fleeing—leaving law enforcement with questions as to the identity of the killer for months. After months of investigation by the FBI and local law enforcement, no one had answers. While the identity of the killer remained unknown, the community became increasingly upset and demanded answers: Who killed those four students? Was the community safe?[2]
In recent years, law enforcement officers have attempted, successfully, to identify unknown suspects through the use of geofencing warrants. Between 2017 and 2018 alone, the number of geofencing warrants received by Google increased by over 1500%, with Google receiving as many as 180 geofencing warrants per week.[3] As courts continue to see an increase in the amount of geofencing warrants submitted by law enforcement, they are forced to maintain a delicate balance of both community safety and the protection of privacy interests for those not suspected of criminal activity. While geofencing warrants may be effective in identifying and locating unknown suspects, they simultaneously pose a myriad of constitutional issues with which courts have struggled to answer. The manner in which these warrants are submitted and executed do not fit within the confines of the Supreme Court’s Fourth Amendment jurisprudence and violate the Constitution.
Part II of this Article discusses the geofencing warrant’s purpose and its ability to assist law enforcement in locating unknown suspects. It also discusses Google’s three-step process associated with geofencing. Part III gives a detailed summary of the two most recent United States District Court opinions involving geofencing warrants. Part IV discusses the constitutional standards for search and seizure and probable cause while providing analysis on whether geofencing warrants fall within the limits of the United States Supreme Court’s Fourth Amendment jurisprudence. Part IV continues by examining historical and modern technology as they relate to third-party doctrine. Part IV also discusses the third-party doctrine’s applicability under Google’s current structure for approving geofencing warrants. Part IV provides a discussion on particularity while providing analysis on particularity under both an originalist and non-originalist approach to constitutional interpretation. Part V discusses circumstances in which geofencing warrants may comply with the Fourth Amendment by providing examples and suggestions. Lastly, Part VI concludes that geofencing warrants, as currently structured by Google and used by law enforcement, are unconstitutional under the Supreme Court’s Fourth Amendment jurisprudence.
Geofencing warrants are used by law enforcement agencies to locate suspects in criminal cases whose identities are unknown at the time of the initial investigation. Google first started receiving geofencing requests as early as 2016, and they currently make up more than 25% of all warrant requests they receive in the United States.[4] The warrants, which are signed by a judge and sent to Google for review, ultimately compel Google to hand over account-identifying information obtained through a user’s location history stored in Google’s Sensorvault.[5] Essentially, law enforcement’s objective is to gather location history data associated with Google users in a particular geographic location over a particular point in time. Although location history is turned off by default, users may turn on location history in their settings, or by downloading Google-based applications on their phones such as Google Maps or Google Photos.[6] Additionally, location history continues to track your information even if the application is deleted or if the user is logged into another device under the same account name.[7] This occurs because location history is tied to an individual user’s account, not their device or the application being used.[8] A user’s location history, which tracks location approximately every two minutes, can help identify potential witnesses or suspects involved in the case by estimating a user’s location with accuracy up to three meters.[9]
The picture below is a depiction of a geofence after law enforcement enters Google’s data into its own mapping software to visualize the desired data points.[10]
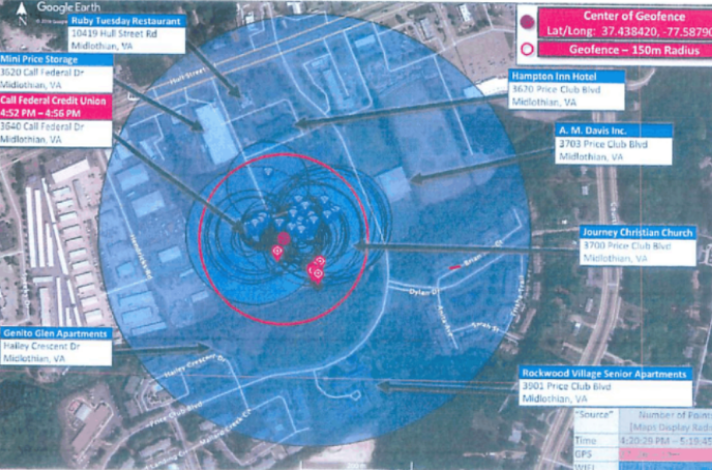 Figure 1. Depiction of a Geofence
Figure 1. Depiction of a Geofence
Google lays out a three-step process required for approval of all geofencing warrants submitted by law enforcement agencies:
During Step 1, law enforcement sends Google their signed geofencing warrant, compelling Google to disclose a “de-identified” list of all Google users whose location history indicates they were inside the geofence boundaries during the specified time frame.[11] In response, Google is required to search all location history data stored in the Sensorvault in order to identify all possible devices that were present within the geographic area during the requested timeframe.[12] “De-identified” data includes the following information: device numbers, latitude/longitude coordinates and timestamps of the stored location history data, the map’s confidence interval, and the sources of the stored location history.[13] Sources of location history include whether the location was generated via Wi-Fi, GPS, or cell tower.[14] While the size of the geographic area and the duration of the timeframe vary by request, Google does not impose restraints on the size of the geographic areas or the lengths of the timeframes.[15] After the initial review of the warrant by a Google specialist, the specialist may seek further information from the law enforcement agency that submitted the warrant and will ultimately consult with Google’s legal counsel.[16] Assuming there are no further concerns, it is at this point that Google will turn over the de-identified information sought out during Step 1.[17]
Step 2, which is designed to allow law enforcement to narrow their search, gives law enforcement an opportunity to review the de-identified information in order to determine the device numbers of interest, which again will vary by request.[18] If deemed necessary after review, law enforcement may compel Google to provide additional location information such as information beyond the geographical and timeframe parameters that were in the original request.[19] This additional information is intended to help law enforcement eliminate devices they consider to not have been in the “target location” for a long enough time to be of interest to the investigation.[20] Google imposes no geographical limits on agencies that seek to expand the geofence during Step 2; however, the expansion of the geofence boundaries must be used so that it only affects the narrow number of device users for which law enforcement is seeking the Step 2 data.[21] Google does not have a policy in place that describes when a request is sufficiently narrow.[22] Similar to Step 1, assuming that Google has no further concerns over the request, they will provide law enforcement with the de-identified, but this time expanded, geographical information.[23]
Google’s process for Step 3 is short and relatively simple. Drawing from the de-identified data that Google has already produced, law enforcement will compel Google to turn over “account-identifying” data for users that law enforcement believes are relevant to the investigation.[24] “Account-identifying” data includes the names and email addresses associated with the Google accounts.[25] Although not required, Google seems to prefer Step 3 data to be narrowed following the Step 2 request.[26] This information, when used in conjunction with various other investigative techniques, is effective in helping law enforcement track down potential suspects and witnesses to a case.
In light of this new technology, criminal defendants are challenging geofencing warrants as unconstitutional, specifically relying on third-party doctrine and the Fourth Amendment’s particularity requirement. While only a handful of trial courts have heard these geofencing challenges, their opinions highlight the difficulty in applying Fourth Amendment doctrine to cases that involve geofencing technology. The two most recent cases, United States v. Chatrie and United States v. Davis, explored the issues surrounding third-party doctrine and particularity. The Court in both cases ultimately ruled in favor of the Government—not because the warrants themselves were constitutional—but because of the good faith exception.
In United States v. Chatrie, the United States District Court for the Eastern District of Virginia held the geofencing warrant at issue to be unconstitutional under the Fourth Amendment to the United States Constitution because the warrant lacked particularity to search all nineteen users within the geographical area requested by law enforcement.[27] The court did not believe that Steps 2 and 3 fixed the particularity issue, holding:
And to the extent the Government would argue that Steps 2 and 3 cure the warrant’s defects as to probable cause, such an argument is unavailing here. The Government itself contends that law enforcement demonstrated probable cause to obtain all the data sought without any narrowing measures (i.e., de-anonymized and geographically unlimited data from everyone within the geofence). In any event, Steps 2 and 3—undertaken with no judicial review whatsoever—improperly provided law enforcement and Google with unbridled discretion to decide which accounts will be subject to further intrusions. These steps therefore cannot buttress the rest of the warrant, as they fail independently under the Fourth Amendment’s particularity prong.[28]
The Chatrie court was unsure of the applicability of the third-party doctrine and was skeptical of the doctrine’s applicability under the Supreme Court’s modern-day jurisprudence as it relates to geofencing warrants. “The Court simply cannot determine whether Chatrie ‘voluntarily’ agreed to disclose his Location History data based on this murky, indeterminate record. But the court expresses its skepticism about the application of the third-party doctrine to geofence technology.”[29] Ultimately, the Chatrie court denied the motion to suppress the evidence obtained by the geofencing warrant, citing to the good faith exception outlined in United States v. Leon.[30]
Unlike Chatrie, in United States v. Davis the court refused to analyze whether the geofencing warrant at issue lacked probable cause because the court held that the defendant lacked standing to challenge the warrant and that the warrant was carried out in good faith under Leon.[31] “Even assuming arguendo that the Google II Warrant lacked particularity, there is nothing in the record to suggest that [investigator] Faggert’s reliance on the warrant was objectively unreasonable. Because there is no law enforcement wrongdoing to deter, suppression is not warranted.”[32]
Additionally, the Davis court stated that the holding in Carpenter[33] need not apply in certain situations:
[G]eofence warrants seeking information for the time periods contained in the Google II Warrant—all under
forty-five minutes—are not covered by Carpenter. The information sought by such warrants, is however, analogous to the historical location data considered in Carpenter. As Davis acknowledged during the evidentiary hearing, this Court is in “uncharted territory” in light of the paucity of decisions in this Circuit, and nationwide, available to guide the court’s evaluation of the Google II Warrant.[34]
Fundamental in protecting the American people from unlawful searches carried out by law enforcement is the Supreme Court’s constitutional standard first mentioned in Katz v. United States.[35] An act on behalf of law enforcement is considered a search within the meaning of the Fourth Amendment when there is a reasonable expectation of privacy in the person or area being searched.[36] Only when a reasonable expectation of privacy has been established will law enforcement then be required to obtain a warrant, supported by probable cause, in order to lawfully carry out that search.[37]
In Katz, the government attached an electronic listening and recording device to the outside of the public telephone booth from which the petitioner had placed his phone calls.[38] The Court held that these eavesdropping activities by the government constituted a “search and seizure” within the meaning of the Fourth Amendment.[39] Justice Harlan’s concurring opinion set forth the two-part test.[40] This test, containing both a subjective and objective prong, has been adopted by the Court and is the governing rule that applies to Fourth Amendment search and seizure analysis.[41] First, the person must have exhibited an actual (subjective) expectation of privacy.[42] Second, the person must have shown an objective expectation of privacy that society is prepared to deem as “reasonable.”[43]
Under Katz, users who are subject to geofencing searches must first show that they have a subjective and objective expectation of privacy in the location information being stored by Google. Even if the government attempts to argue that there is no reasonable expectation of privacy in a person’s physical movements while out in public, there still might be Google users residing in their own homes with location history turned on during the geofencing time frame. If this two-prong test is satisfied, turning over that location information to law enforcement is then considered a search within the meaning of the Fourth Amendment, triggering the warrant requirement. To comply with the Fourth Amendment’s warrant requirement, the process by which law enforcement obtains that location information from Google will always be subject to a warrant supported by probable cause and signed by a detached and neutral magistrate.[44]
As technology has become more advanced, the Supreme Court has struggled to balance the government’s interest in prosecuting crime with the privacy interests of the American people. This balance has proven to be no easy task as technology develops over time, presenting law enforcement with a wide range of opportunities when conducting criminal investigations. As the Supreme Court has gone through growing pains in their pursuit to find the proper balance between technology and the Fourth Amendment, the introduction of geofencing warrants has left lower courts confused as to how this new technology fits within the Court’s Fourth Amendment jurisprudence.
Helpful in reviewing the evolution of technology is the Supreme Court’s opinion in Smith v. Maryland, where the Court struggled to apply the third-party doctrine when law enforcement used pen register technology to conduct a warrantless search on a person’s numbers dialed from his phone.
In Smith, a woman was robbed by a defendant who proceeded to harass her through numerous threatening and obscene phone calls.[45] The defendant’s telephone company, per the request of law enforcement, installed a pen register device at its main office in order to record the numbers dialed from his phone telephone.[46] The Smith Court was tasked with determining whether the installation and use of a pen register device constituted a “search” within the meaning of the Fourth Amendment.[47] The Court held that a person does not have a reasonable expectation of privacy in the numbers dialed from a phone and that the installation and subsequent use of a pen register device by law enforcement was not a search or seizure within the meaning of the Fourth Amendment, bypassing the warrant requirement and relieving law enforcement of their constitutional duty to establish probable cause.[48] The Court went as far as to say that even if a person has an actual, subjective expectation of privacy in the numbers they dial into a phone, that expectation is not legitimate.[49] The Court rationalized its decision through the application of the third-party doctrine, which states that people do not have a legitimate expectation of privacy in the information voluntarily given to a third-party.[50]
Applying third-party doctrine to phone calls, the Court reasoned: “When he used his phone, petitioner voluntarily conveyed numerical information to the telephone company and ‘exposed’ that information to its equipment in the ordinary course of business. In so doing, petitioner assumed the risk that the company would reveal to police the numbers he dialed.”[51]
The dissenters in Smith, however, were not convinced that the numbers dialed from a private phone fell outside the constitutional protections of the Fourth and Fourteenth Amendments, citing to the holding in Katz where the Court made clear that telephone conversations carried out by people in their homes or offices are constitutionally protected.[52] The dissent in Smith attacked the majority’s use of the third-party doctrine by explaining that, although the numbers dialed are recorded for billing purposes,
that observation no more than describes the basic nature of telephone calls. A telephone call simply cannot be made without the use of telephone company property and without payment to the company for the service . . . . [W]e have squarely held that the user of even a public telephone is entitled “to assume that the words he utters into the mouthpiece will not be broadcast to the world.”[53]
The phone numbers obtained through these pen registers, the dissent claimed, is information with which the phone subscriber has a legitimate expectation of privacy, regardless of whether or not it is obtained by a trespass.[54] The dissent continued to attack the majority’s application of the third-party doctrine by stating that, even though most private telephone subscribers may have their own numbers listed in a public directory, “I doubt there are any who would be happy to have broadcast to the world a list of the local or long distance numbers they have called.”[55]
In United States v. White, the Court again found itself with the task of balancing the principles of third-party doctrine and technology. In White, law enforcement used radio transmitters concealed on a government informant to relay conversations that took place between the defendant and the informant inside the informant’s home.[56] These conversations were relayed through the concealed transmitters and overheard by an agent hiding in the kitchen closet and a second agent outside the house using a radio receiver.[57]
The Court held that the Fourth Amendment does not bar from evidence the testimony of police officers who use recorded conversations obtained through electronic surveillance, holding it constitutional under the third-party doctrine and, again, bypassing the need for a warrant supported by probable cause.[58] The Court rationalized its holding by claiming:
If the conduct and revelations of an agent operating without electronic equipment do not invade the defendant’s constitutionally justifiable expectations of privacy, neither does a simultaneous recording of the same conversations made by the agent or by others from transmissions received from the agent to whom the defendant is talking and whose trustworthiness the defendant necessarily risks.[59]
The Court went on to say, “If the law gives no protection to the wrongdoer whose trusted accomplice is or becomes a police agent, neither should it protect him when that same agent has recorded or transmitted the conversations which are later offered in evidence to prove the State’s case.”[60] Moreover, the Court used the Fourth Amendment’s “fluid concepts of ‘reasonableness’” to rationalize its claim that evidence obtained through law enforcement agents equipped with surveillance technology versus agents not equipped with such technology does not require any form of “discrete constitutional recognition.”[61] Interestingly, the majority in White considered the accuracy and reliability of evidence obtained under the third-party doctrine as part of its analysis: “Nor should we be too ready to erect constitutional barriers to relevant and probative evidence which is also accurate and reliable. An electronic recording will many times produce a more reliable rendition of what a defendant has said than will the unaided memory of a police agent.”[62]
Advancements in modern technology give law enforcement the ability to obtain significantly greater volumes of information than ever before. This increase in volume of information, whether obtained through GPS, cell site data, or geofencing, has stretched the limits of the Constitution. The Court is forced to reconsider how to apply Fourth Amendment law under these new circumstances to determine whether or not a search has been conducted. The Supreme Court also wrestled with determining where third-party doctrine falls in the Court’s current Fourth Amendment jurisprudence. In both United States v. Jones and Carpenter v. United States, the Court struggled with the intersection of technology and third-party doctrine as they related to issues concerning Global Positioning System (GPS) technology and Cell Site Location Information (CSLI).[63]
The Supreme Court’s unanimous holding in United States v. Jones brought to light the Court’s willingness to draw a constitutional line between modern technology and the Fourth Amendment. In Jones, federal agents installed a GPS tracking device on Jones’s vehicle while it was parked in a public parking lot. Over the course of twenty-eight days, law enforcement used the device to track the vehicle’s movements.[64] The Court in Jones was tasked with determining whether the attachment of a GPS tracking device to a person’s vehicle, and subsequent use of that device to monitor the vehicle’s movements on public streets, constituted a search or seizure within the meaning of the Fourth Amendment.[65] The Court held that it did, but not for principles related to reasonable expectation of privacy.[66]
Although the majority in Jones arrived at its holding through the principles of trespass, Justice Sotomayor’s concurring opinion highlights a crack in the Court’s third-party doctrine in cases involving modern technology. Sotomayor firmly believed that the attributes of GPS monitoring should be taken into account when considering the existence of a reasonable expectation of privacy in an individual’s public movements[67]:
I would take these attributes of GPS monitoring into account when considering the existence of a reasonable societal expectation of privacy in the sum of one’s public movements. I would ask whether people reasonably expect that their movements will be recorded and aggregated in a manner that enables the government to ascertain, more or less at will, their political and religious beliefs, sexual habits, and so on.[68]
Notably, Justice Alito concurred in the judgment for reasons similar to Sotomayor.[69] Sotomayor’s concurring opinion in Jones also addressed the “voluntary” collection of electronic information unbeknownst to the subject of the warrant:
More fundamentally, it may be necessary to reconsider the premise that an individual has no reasonable expectation of privacy in information voluntarily disclosed to third parties. This approach is ill suited to the digital age, in which people reveal a great deal of information about themselves to third parties in the course of carrying out mundane tasks. People disclose the phone numbers that they dial or text to their cellular providers; the URLs that they visit and the e-mail addresses with which they correspond to their Internet service providers . . . .[70]
The Court revisited this same concern in Carpenter, where the Court again reviewed the intersection between modern technology and the Fourth Amendment. The Court in Carpenter held that an individual maintains a legitimate expectation of privacy in the record of his physical movements as captured through cell site location information, and the acquisition of this information is considered a search within the meaning of the Fourth Amendment.[71] The Court, struggling to apply existing third-party doctrine to resolve the CSLI issue, explained, “This sort of digital data—personal location information maintained by a third party—does not fit neatly under existing precedents. Instead, requests for cell-site records lie at the intersection of two lines of cases, both of which inform our understanding of the privacy interests at stake.”[72] The Court went on to say:
[W]hile the third-party doctrine applies to telephone numbers and bank records, it is not clear whether its logic extends to the qualitatively different category of cell-site records. After all, when Smith was decided in 1979, few could have imagined a society in which a phone goes wherever its owner goes, conveying to the wireless carrier not just dialed digits, but a detailed and comprehensive record of the person’s movements . . . . [T]he fact that the information is held by a third party does not by itself overcome the user’s claim to Fourth Amendment protection.[73]
The Court in Carpenter laid out two points undermining the argument that third-party doctrine applies to warrantless searches of a person’s CSLI. First, the Court noted that CSLI does not just track a person’s movements at a specific point in time; rather, it tracks a person’s movements over days and years, leading to privacy concerns “far beyond those considered in Smith . . . .”[74] Second, the Court said that the “voluntary exposure” aspect of third-party doctrine does not hold up when it comes to CSLI searches by claiming that phone location information is shared by no affirmative act on behalf of the user itself other than simply powering on the device.[75] “As a result, in no meaningful sense does the user voluntarily ‘assume the risk’ of turning over a comprehensive dossier of his physical movements.”[76]
Today, the intersection of third-party doctrine and modern technology presents a major cause for concern because of the massive volume of information available to law enforcement. Because Google is witnessing an exponential increase in the number of geofencing warrants submitted by law enforcement,[77] lower courts are now forced to determine the most appropriate way, if any, of applying third-party doctrine in geofencing cases.
Historical cases such as Smith and White, where the Court applied third-party doctrine in favor of the government, are not factually similar to cases involving geofencing. In Smith and White, only one person’s privacy rights were at stake, whereas in geofencing cases multiple people’s privacy rights are at stake. The privacy issues in Smith and White are also distinct from cases involving geofencing warrants because people today hold significantly greater privacy interests in the information stored in Google’s Sensorvault compared to phone numbers stored in pen registers or words spoken to a third person. Using these historical cases will not help the courts determine the applicability of third-party doctrine for geofencing warrants.
Cases that deal with law enforcement’s reliance on modern technology, such as Jones and Carpenter, are more relevant in helping lower courts determine whether application of third-party doctrine is appropriate in geofencing cases.[78] The government’s reliance on third-party doctrine may seem applicable because users are required to “opt in” on their phones before sharing their location information with Google. However, courts should apply the reasoning in Jones and Carpenter to prevent law enforcement from executing geofencing warrants under third-party doctrine for two reasons.
First, the privacy interests at stake in geofencing cases are even greater than what the Court dealt with in Jones and Carpenter. Similar to Smith and White, both Jones and Carpenter dealt with only one person’s information being turned over and searched by law enforcement. When Google approves a geofencing warrant, they are consequently turning over multiple people’s private information to law enforcement. Unlike location information obtained through GPS monitoring or CSLI data, which targets only one person, there are no limits as to how many users can be the target of a geofencing warrant.[79] Applying third-party doctrine to Google’s three-step process allows geofencing warrants to function as unconstitutional general warrants.[80] Depending on the location, hundreds, if not thousands, of people not suspected of committing crimes are subject to their location history being turned over by Google.[81]
Second, persons subject to geofencing warrants could not have reasonably understood the long-term implications of what they were “voluntarily” turning over when they “opted in” to share location history with Google. In Jones, Justice Sotomayor’s concurring opinion mentions a “reasonable societal expectation of privacy in the sum of one’s movements.”[82] In today’s society, our phones function as an extension of our person.[83] Almost every member of society carries with them a cell phone that contains endless amounts of private, intimate information.[84] Not only is the volume of information endless, but this information is routinely being shared with third parties, unbeknownst to the user. No person reasonably expects their location history information, which is tracked every two minutes by Google, to be stored and then used by law enforcement in situations where they are not the target of a criminal investigation.[85] Nothing about this information has been given up “voluntarily” by the user.
The Court’s reasoning in Carpenter that “voluntary exposure” need not apply due to a lack of any affirmative act taken on behalf of users who “powered up” their cell phones should be extended to the application of third-party doctrine in geofencing cases.[86] While Google users do “opt in” to share their location history through the single click of a button, “opting in” is no more of an affirmative act than “powering up” a cell phone. Both acts take mere seconds, and in both cases, users are completely unaware of the extent to which their information is being stored for future use by law enforcement. Users who “opt in” to sharing location history when using a Google device could not have reasonably known the extent to which their location information would be stored by Google and subsequently used by law enforcement for criminal investigations. In no meaningful sense have Google users assumed this risk. It is unreasonable to assume that any member of society is actually aware, or should be aware, that Google continues to track a user’s location history on other devices, under the same account, even when a Google application is deleted.
To comply with the Fourth Amendment’s warrant requirement, all warrants must contain probable cause, supported by oath or affirmation, and particularly describe the places to be searched and items to be seized.[87] Additionally, the probable cause itself must be particularized with respect to the persons to be searched or seized.[88] If courts in the future hold that third-party doctrine does not apply in geofencing cases, then law enforcement must establish particularity as to every person that lies within the geofence in order to satisfy the warrant requirement.
Under Google’s current three-step process, the particularity requirement presents two issues for law enforcement. First, at the time geofencing warrants are submitted to Google, law enforcement cannot possibly establish probable cause because they are completely unaware of the identities of the both the suspects and everyone else that lies within the geofence. Even through Google’s narrowing procedure in Step 2, the revised geofencing warrant has the potential to include other people’s location information who were not targets of the investigation. Even if law enforcement somehow established probable cause for the specific people suspected of the crime, the warrant fails to establish any semblance of particularized probable cause as to everyone else whose location falls within the geofence. Law enforcement officers have no reason to believe that everyone inside the geofence has committed, or has been associated with, the crime. Second, to satisfy particularity, the geofencing warrant must particularly describe everyone who lies within the geofence—an impossible task without knowing the identity of everyone inside the geofence. Law enforcement’s reliance on the principles of third-party doctrine is not enough—these warrants must be sufficiently particular to the places, persons, or things being searched.[89] Without establishing particularity for every Google user included in the geofence, geofencing warrants fail to satisfy the Fourth Amendment’s particularity requirement.
Competing methods of constitutional interpretation often force judges to arrive at drastically different legal conclusions depending on their preferred method of interpretation: originalism and non-originalism. Judges that apply the principles of originalism are of the belief that the words of the Constitution are to be given the meanings they were popularly understood to have when the relevant provision was adopted.[90] A slightly different view of originalism is the belief that the text of the Constitution should be interpreted to effectuate the intent of those who framed the provision in question. Regardless of these two slight variations, judges that apply originalism as their preferred method of constitutional interpretation resort to using an in-depth historical analysis to arrive at their conclusions.[91] In contrast, judges that apply principles of non-originalism, often referred to as “living constitutionalism,” are of the belief that the Constitution need not be interpreted in accordance with the text’s original meaning, intention, or understanding of its framers or ratifiers.[92] Rather, new meanings may be given to the text of the Constitution to accord with the times and reflect contemporary understandings of modern society.[93]
While nearly all constitutional interpretation issues hinge on a judge’s application of originalism or non-originalism, “particularity” in the context of geofencing warrants seems to be an outlier. Under both originalism and non-originalism, a geofencing warrant’s particularity presents a major constitutional issue that cannot be resolved by either method of constitutional interpretation to fit within the bounds of the Fourth Amendment.
One of the fundamental concerns that led to the establishment of the Fourth Amendment’s particularity requirement was the Framers’ fear of general warrants. In other words, the Framers were fearful that the government would allow general searches of its citizens without establishing probable cause.[94] “Our cases have recognized that the Fourth Amendment was the founding generation’s response to the reviled ‘general warrants’ and ‘writs of assistance’ of the colonial era, which allowed British officers to rummage through homes in an unrestrained search for evidence of criminal activity.”[95]
When considering both the original meaning and intent of the Fourth Amendment’s particularity requirement at the time of its adoption, geofencing warrants fail under an originalist approach. It is difficult to imagine that the Framers would have approved of these geofencing warrants, which are essentially being used as general warrants by giving law enforcement the ability to search wide geographic areas over large amounts of time without establishing probable cause as to any particular suspect. The Framers’ fear that underscored general warrants was the concern that general warrants infringed on the privacy rights of American citizens who were not suspected of committing a crime. But geofencing warrants do exactly that—infringing on privacy rights by placing broad-sweeping geofences over densely-populated buildings with the hopes of seizing everyone’s location information that lies within the geofence in order to track down and identify unknown suspects.[96] These actions are contrary to the Framers’ intentions. By taking their fear of general warrants into consideration when analyzing particularity, an originalist approach supports the conclusion that there is no practical difference between general warrants and geofencing warrants. Under originalism, geofencing warrants are unconstitutional for failure to satisfy particularity under the Fourth Amendment.
As technology evolves, our privacy interests become more vulnerable to exploitation by law enforcement. The primary concern of judges that apply non-originalism is to ensure that the meaning of the text accurately reflects contemporary views of society at the time the text is being interpreted. The Supreme Court’s jurisprudence has, at times, adopted a “living Constitution” approach to constitutional interpretation.[97] The Court’s own website endorses the same:
The complex role of the Supreme Court in this system derives from its authority to invalidate legislation or executive actions which . . . conflict with the Constitution. This power of “judicial review” has given the Court a crucial responsibility in assuring individual rights, as well as in maintaining a “living Constitution” whose broad provisions are continually applied to complicated new situations.[98]
When taking into account modern views of society, judges that apply a non-originalist approach would scoff at the notion that geofencing warrants satisfy “particularity” under the Fourth Amendment. Neither the Framers’ intent at the adoption of the Fourth Amendment’s warrant requirement nor any other historical analogues are necessary to arrive at this conclusion. As law enforcement’s ability to conduct lawful searches develops over time by way of advanced technology, judges that embrace a non-originalist view are tasked with interpreting the Fourth Amendment’s “particularity” language in a manner that accurately reflects modern views of society. Because most Americans own smartphones that contain a functionally infinite supply of private information,[99] it is reasonable to assume that nearly all members of society have developed a privacy interest in the information stored on their phones.[100] Given that geofencing technology allows law enforcement to search any and all Google user’s location information within a certain geographic area, a non-originalist method of interpretation would require that geofencing warrants be “particular” as to the suspects whose location information is being searched. Attempting to establish probable cause by simply placing a geofence over a known location without particularly describing the suspects being searched fails to satisfy particularity when taking into account modern beliefs about privacy. By nature of their intended use, geofencing warrants are only executed when the suspects are unknown to law enforcement.[101] It necessarily follows that, under a non-originalist approach, geofencing warrants violate the Fourth Amendment for failing to particularly describe what exactly is being searched.
Notwithstanding the aforementioned constitutional hurdles, there may be a handful of narrow circumstances where geofencing warrants fall within the bounds of the Fourth Amendment.[102] While maybe few and far between, these narrow circumstances demonstrate the geofencing warrant’s unique and efficient ability to solve difficult issues that arise when law enforcement officers fail to identify suspects involved in a crime. The following two scenarios demonstrate situations where a geofencing warrant would likely pass constitutional muster and satisfy the Fourth Amendment’s warrant requirement:
One might imagine a situation where the person suspected of committing a crime did so with no one else around them. In this scenario, a family away on vacation is notified by their home security system (connected to their phones) that someone has trespassed onto their property at around 2:00 pm. The family confirms with law enforcement that no one was permitted to be inside their home at the time of the incident. After the investigation, law enforcement reports that, although no one nearby identified the suspect, they obtained security footage of the suspect leaving the home one hour later, wearing a mask. Given that the suspect is now unknown, this presents a prime opportunity for law enforcement to execute a geofencing warrant to assist in identification of the suspect.[103] At this stage, law enforcement can narrowly define their geofence parameters to include only the home and the time period that captures the suspect’s entry and exit of the home. Given the fact that only one person was present in the home at the time of the crime, it can be established that the only privacy data being searched is that of the suspect. Under these narrow circumstances, where law enforcement establishes probable cause that only the unknown suspect was present at the time of the crime, the geofencing warrant passes constitutional muster and satisfies particularity. There is no need to address the concerns relating to particularity outlined in Chatrie, because the only location information being searched is that of the lone suspect.[104]
Similar to Scenario 1, we can imagine a situation where a suspect commits a crime in a house with only a limited number of people living inside.[105] In this scenario, the suspect enters the home of six college students in the middle of the night, killing four of them while sparing the other two. After murdering the four roommates, the suspect leaves and is not identified. Law enforcement establishes probable cause, based on the evidence at the scene of the crime, that someone entered the apartment and committed quadruple homicide. In an attempt to identify the unknown suspect, law enforcement places a narrowly defined geofence over the home with a timeframe that covers the middle of the night through the early morning hours. In this situation, only three people are subject to having their location history searched by the warrant: the suspect himself and both surviving roommates. Here, the geofencing warrant should be upheld because the size of the area being searched is narrowly defined and the privacy risk to those not involved in the crime is minimal. Even if the court takes issue with the two unsuspected roommates being exposed to the search, law enforcement can remedy the situation in Step 2 by narrowing down the anonymized information and requesting only the necessary account-identifying information in Step 3. The warrant at issue here in Scenario 2 is also sufficiently distinct from the particularity issues raised by the court in Chatrie, which dealt with a geofence that covered 70,686 square meters of land and a bank with dozens of customers inside.[106]
Although both Scenarios 1 and 2 are sufficiently narrow, courts are still concerned about law enforcement’s unbridled discretion with executing Steps 2 and 3 in a single warrant.[107] “In other words, ‘[a] warrant that meets the particularity requirements leaves the executing officer with no discretion as to what to seize.’”[108] If courts are truly concerned about particularity, then judges must play a bigger role by requiring law enforcement to obtain new warrants at each step of the process that specifically describe what is being searched. The warrant must be particular each time it is submitted to a magistrate for review and not as a result of engaging in a post-hoc narrowing of information after the judge has already signed it.[109] After sending a geofencing warrant to Google, Step 1 is complete when Google searches their Sensorvault and produces a list of the anonymized information to law enforcement. However, Steps 2 and 3—which allow law enforcement to review the anonymized data and request additional information before receiving names and email addresses associated with the accounts[110]—often leave officers with “unbridled discretion and lack any semblance of objective criteria to guide how officers would narrow the lists of users.”[111] While some geofencing warrants explicitly provide for these extra steps, many do
not—and Google continues to participate in them despite not being legally required to by a court.[112]
Requiring a new warrant at each step of the process would remove law enforcement’s unbridled discretion by requiring that each geofencing step is independently reviewed by a magistrate before moving on to the next step of the search.[113] This would not only help cure the particularity issue, but also help to protect against overbreadth by acting as a court-supervised filter in order to minimize third-party privacy concerns.[114] Step 1 warrants should only be focused on seizing anonymized information obtained through Google’s search of their Sensorvault, and should law enforcement feel the need to obtain identifying information based on the data in the Step 1 warrant, they can bring that information to the court and obtain a new warrant for Steps 2 and 3.
Scenarios 1 and 2 both demonstrate specific instances in which geofencing warrants would likely face little to no constitutional hurdles. Although Scenario 1 may be uncommon, Scenario 2 highlighted a much more common situation encountered by law enforcement: an unknown suspect committing a crime with only a limited number of people who were present in the geofence. In situations similar to Scenario 2, law enforcement must do more than simply argue that the geofence is sufficiently narrow—they must establish particularity at each step of the process. As these warrants become more popular, courts will begin to question the applicability of good faith and third-party doctrines as methods that help law enforcement circumvent the Fourth Amendment’s warrant requirement. The only plausible way that courts in the future will approve geofencing warrants is if (1) they’re being used in situations where the risk of obtaining other people’s information is low, as seen in the scenarios above, and (2) if law enforcement obtains a new warrant at each step along the way.
Under the Supreme Court’s Fourth Amendment jurisprudence, geofencing warrants as they are currently used by law enforcement are unconstitutional. The Court’s two-prong test, used to analyze issues of search and seizure, determines whether a person subject to a geofencing search had both a subjective and objective expectation of privacy in their location history. Although the principles of trespass do not apply to those affected by geofencing warrants, it is clear that Google users have both an objective and subjective expectation of privacy in their location history information stored by Google in the Sensorvault.
The Court’s third-party doctrine should not apply in geofencing cases because there is no sufficient affirmative act on behalf of Google users to voluntarily turn over their location history information to Google. Even with this information being shared with Google, users could not have reasonably known the extent to which their information is being stored and subsequently used by law enforcement in future criminal investigations. Because Google users retain a reasonable expectation of privacy in their location history information, geofencing warrants must particularly describe the persons to be searched, be supported by particularized probable cause, and signed by a detached and neutral magistrate judge.
If law enforcement wishes to continue locating and identifying unknown suspects through the use of geofencing warrants, then there needs to be a heightened sense of urgency in correcting these deficiencies. These re-structured geofencing warrants need not only be sufficiently narrow in their scope as to location and time, but they must be submitted and signed by a judge at each step of Google’s three-step process. Once law enforcement loses the protection of good faith and third-party doctrine, the geofencing warrant’s lack of particularity will force courts in the future to render these warrants unconstitutional.